
Feature image: FROM LEFT: DOMENIC FORTE, PH.D., STEVEN A. YATAURO FELLOW AND ASSOCIATE PROFESSOR IN THE DEPARTMENT OF ELECTRICAL AND COMPUTER ENGINEERING; DAMON WOODARD, PH.D., DIRECTOR OF THE FLORIDA INSTITUTE FOR NATIONAL SECURITY AND ASSOCIATE PROFESSOR IN THE DEPARTMENT OF ELECTRICAL AND COMPUTER ENGINEERING; AND RONALD WILSON, PH.D., POST-DOCTORAL RESEARCHER IN ELECTRICAL AND COMPUTER ENGINEERING
It’s been an issue with integrated circuits (IC) for a long time. While roughly 80 percent of the globe’s intellectual property (IP) is developed in the U.S, more than 80 percent of the chip fabrication is done in Asia, where compromised foundries can insert malware or may heist the embedded IP. End users in inhospitable nation-states can also reverse-engineer chips. And with supply chains languishing due to the pandemic, counterfeiters are rapidly capitalizing on the shortage of microchips by flooding the market with corrupted knockoffs.
“The financial cost of this problem is immense,” said Damon Woodard, Ph.D., director of the Florida Institute for National Security and associate professor in the Department of Electrical and Computer Engineering at the University of Florida (UF). “Intellectual property infringement accounts for multiple billion dollars each year. But more importantly, this is a national security threat. The prospect of a Trojan horse finding its way into some military equipment requires a solution that can verify chip security without the shadow of a doubt that what you’re expecting is what you’re getting.”
Dr. Woodard is leading a $1.2 million, three-year NSF research project to use artificial intelligence for the purpose of hardware security by developing an automated toolkit that will detect intellectual property and verify that the IC designs are exactly what they are supposed to be and not a piracy or sabotage. “In essence, we get the chip, take it apart, and let AI scan it to map the design, then we use the data gathered by the AI to verify whether what is supposed to be there is actually there,” Dr. Woodard explains.
A POWERFUL IN-HOUSE ASSET
The IC images are provided by UF’s FEI Helios Nanolab 600 dual-beam focused-ion beam/scanning electron microscope (FIB/SEM), which offers microchip scans at a resolution of less than one nanometer. “Today’s most advanced chips have features around three nanometers,” said Domenic Forte, Ph.D., Steven A. Yatauro Fellow and associate professor in the Department of Electrical and Computer Engineering, who serves as director of the Florida Institute for CyberSecurity (FICS) Research’s SeCurity and AssuraNce (SCAN) Lab. “To put that in perspective, a human hair is about 60,000 nanometers wide.” A co-PI of the project who focuses on the hardware component, Dr. Forte uses ion beams from the FIB/SEM to gradually oblate the layers of the chip to reveal the next feature below, as it produces scans simultaneously. Then an aggregation of all the images is knitted together, then reverse engineered, to form a replication of the IC guided by AI.
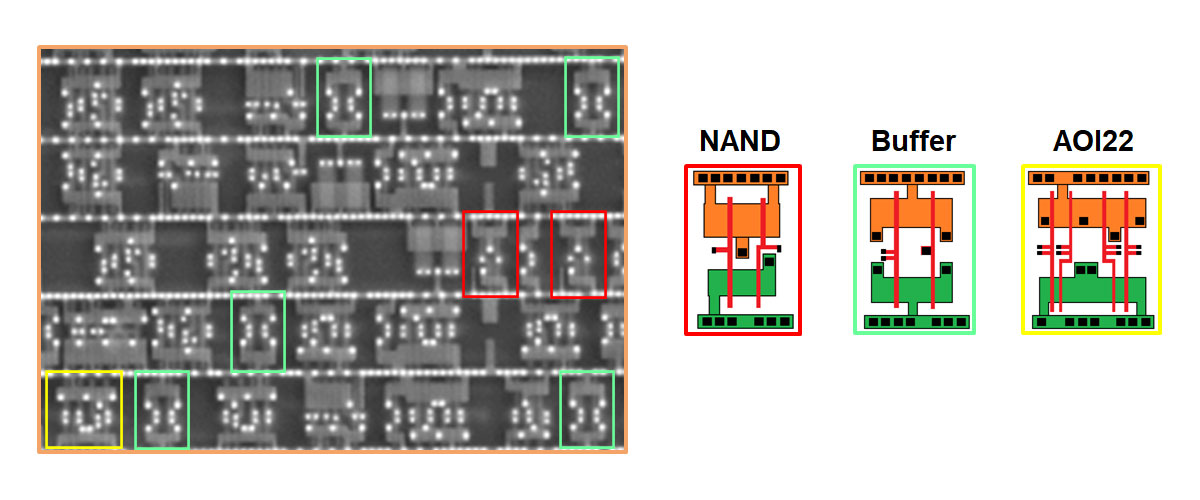
INTEGRATED CIRCUIT CAMOUFLAGING TECHNIQUES PROTECT INTELLECTUAL PROPERTY FROM REVERSE ENGINEERING BY DISRUPTING THE ABILITY OF THE ATTACKER TO IDENTIFY LOGIC GATES FROM THE IMAGES OBTAINED AFTER DELAYERING AND IMAGING.
“Think of it as teleportation — you destroy it in one place and completely recreate it in another,” said Ronald Wilson, Ph.D., a UF post-doctoral researcher in Electrical and Computer Engineering whose work in reverse engineering and building the algorithms fuel the project’s IC security models. “The traditional approach takes a very long time because you’re talking about a circuit design with billions of electronic gates and hundreds of thousands of images. And, because it involves humans, it’s error prone. Automation through AI is much less likely to make those mistakes.”
THE GAME-CHANGING EFFECT OF THE HIPERGATOR
An important facet of the project is developing ‘privacy-preserving transformations,’ replications of the chip data where the instructive elements are present to train the algorithms while obscuring the details of the IP holder’s proprietary design. Companies and defense contractors are not only strict about protecting their property but are bound by strict nondisclosure agreements. “Industry doesn’t want to release all the design information that could make the IP creator vulnerable to piracy,” Dr. Wilson said. Using UF’s data-crunching HiPerGator, his team develops algorithms to disguise the design, giving IP holders a facsimile of the underlying data that helps them improve their IC models without revealing the essential kernel of their sweat equity.
“HiPerGator is the number one thing we have at UF that allows us to pull this off by doing these complex transformations,” Dr. Woodard said. “These models demand highly sophisticated work which requires significant training. That time is reduced by at least half using the supercomputer.”
Renowned for his innovations in facial recognition and deconstructing deep fakes— digitally altered images or videos — Dr. Woodard uses a similar skillset to expand his repertoire into IC security.
“Techniques I’ve learned for facial recognition are directly applicable here,” he said. “In each application, we are working with images which possess less than ideal characteristics. That’s the computer vision aspect — how computers gain high-level learning from vast analysis of images — and it applies here too. In our proposal we intend to generate synthetic data — virtual data that was not captured — to facilitate data-driven approaches to reverse engineering, like we did with deep fakes. Here, we’re applying some of the techniques that we used with deep fakes, of generating fake face images, doing the same thing to generate fake IC/SEM (scanning electron microscope) images. We have a very large and realistic data set to teach the AI what to look for in the design.”
The proposal is a ‘transfer-to-practice’ (TTP) project, one that is farther along in its research progression and fungible by virtue of its demand in the marketplace, having been courted by Battelle, a nonprofit microelectronics interest, Texplained, a French company that specializes in IC reverse engineering, trust/assurance of electronics and evaluation of intellectual property, and TechInsights, the recognized world leader in microelectronics reverse engineering and IP services.
BUILDING A DIVERSE CYBERSECURITY TALENT PIPELINE
As an outreach component of the NSF proposal, Dr. Woodard and his team will recruit four undergraduate students each year from Prairie View A&M’s Secure Center of Excellence, giving them invaluable cybersecurity research experience during the summer session. Preliminary distance learning modules consisting of video lectures and exercises that are based on AI, computer vision, deep learning and hardware security, along with access to research team meetings will be offered to Prairies View students. Through UF’s partnership with the Inclusive Engineering Consortium (IEC) — a collective of 15 HBCUs, three Hispanic-serving institutions and two tribal colleges — Prairie View A&M students will have reciprocal use of HiPerGator at their Houston campus. Dr. Woodard hopes to inspire these students to enroll in graduate studies at UF eventually. “Anything we can do here, they can do there,” he said. “Once they get a taste of this experience, we’d like to see them go to the next level by joining our research community in this crucial work.”
This feature originally appeared in the Herbert Wertheim College of Engineering (HWCOE) Newsletter in May 2022.